Wireshark 3.0.1 (64-bit)
Wireshark 3.0.1 (64-bit)
Wireshark.org - ( Open Source)
Wireshark helps network administrators to solve protocol issues by diagnosing the problems in the software protocols.
Wireshark is a famous network analysis or packet sniffer tool protocols.
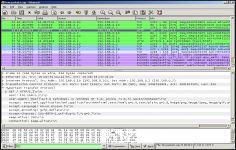
Wireshark examine data from a live network, and can also take a snapshot of the various communications that work on it at another time. Wireshark proposes to see the "dissector tables" directly from the main window. The application can export objects to SMB screen or display the compiled BPF code for capture filters. Finally, Wireshark supports a variety of protocols such as ADwin, Apache Etch, JSON, reload or Wi-Fi P2P (Wi-Fi Direct).
The interface is quite austere, hides an extremely powerful that only experts can use software correctly.
This software is essential for any network administrator to diagnose problems in the software protocols.
- Title:
- Wireshark 3.0.1 (64-bit)
- File Size:
- 56.8 MB
- Requirements:
- Windows XP 64-bit / Vista 64-bit / Windows 7 64-bit / Windows 8 64-bit / Windows 10 / Windows 10 64-bit
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 09 Apr 2019
- Publisher:
- Wireshark.org
- Homepage:
- http://www.wireshark.org/
- MD5 Checksum:
- 8A06061BB19D8FAE7A2536EE84796D7A
Whats New
The Windows installers now ship with Npcap 0.992. They previously shipped with Npcap 0.99-r9.
Bug Fixes
The following vulnerabilities have been fixed:
wnpa-sec-2019-09 NetScaler file parser crash. Bug 15497. CVE-2019-10895.
wnpa-sec-2019-10 SRVLOC dissector crash. Bug 15546. CVE-2019-10899.
wnpa-sec-2019-11 IEEE 802.11 dissector infinite loop. Bug 15553. CVE-2019-10897.
wnpa-sec-2019-12 GSUP dissector infinite loop. Bug 15585. CVE-2019-10898.
wnpa-sec-2019-13 Rbm dissector infinite loop. Bug 15612. CVE-2019-10900.
wnpa-sec-2019-14 GSS-API dissector crash. Bug 15613. CVE-2019-10894.
wnpa-sec-2019-15 DOF dissector crash. Bug 15617. CVE-2019-10896.
wnpa-sec-2019-16 TSDNS dissector crash. Bug 15619. CVE-2019-10902.
wnpa-sec-2019-17 LDSS dissector crash. Bug 15620. CVE-2019-10901.
wnpa-sec-2019-18 DCERPC SPOOLSS dissector crash. Bug 15568. CVE-2019-10903.
The following bugs have been fixed:
[oss-fuzz] UBSAN: shift exponent 34 is too large for 32-bit type 'guint32' (aka 'unsigned int') in packet-ieee80211.c:15534:49. Bug 14770.
[oss-fuzz] UBSAN: shift exponent 35 is too large for 32-bit type 'int' in packet-couchbase.c:1674:37. Bug 15439.
Duplicated TCP SEQ field in ICMP packets. Bug 15533.
Wrong length in dhcpv6 NTP Server suboption results in "Malformed Packet" and breaks further dissection. Bug 15542.
Wiresharks speaker-to-MaxMind is burning up the CPU. Bug 15545.
GSM-A-RR variable bitmap decoding may report ARFCNs > 1023. Bug 15549.
Import hexdump dummy Ethernet header generation ignores direction indication. Bug 15561.
%T not supported for timestamps. Bug 15565.
LWM2M: resource with \r\n badly shown. Bug 15572.
When selecting BSSAP in 'Decode As' for a SCCP payload, it uses BSSAP+ which is not the same protocol. Bug 15578.
Possible buffer overflow in function ssl_md_final for crafted SSL 3.0 sessions. Bug 15599.
Windows console log output delay. Bug 15605.
Syslog dissector processes the UTF-8 BOM incorrectly. Bug 15607.
NFS/NLM: Wrong lock byte range in the "Info" column. Bug 15608.
randpkt -r causes segfault when count > 1. Bug 15627.
Tshark export to ElasticSearch (-Tek) fails with Bad json_dumper state: illegal transition. Bug 15628.
Packets with metadata but no data get the Protocol Info column overwritten. Bug 15630.
BGP MP_REACH_NLRI AFI: Layer-2 VPN, SAFI: EVPN - Label stack not decoded. Bug 15631.
Buildbot crash output: fuzz-2019-03-23-1789.pcap. Bug 15634.
Typo: broli brotli. Bug 15647.
Wrong dissection of GTPv2 MM Context Used NAS integrity protection algorithm. Bug 15648.
Windows CHM (help file) title displays quoted HTML characters. Bug 15656.
Unable to load 3rd party plugins not signed by Wiresharks codesigning certificate. Bug 15667.
Related software
2.0/5 from 172 users