TrueCrypt 4.3a
TrueCrypt 4.3a
TrueCrypt Foundation - (Open Source)
Encrypting a USB key or a whole disk or even creating virtual encrypted disks, all these are possible with TrueCrypt.
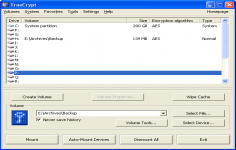
TrueCrypt is a solution for storing encrypted information, allowing to create encrypted virtual disks. When mounted, the media appear in Explorer as a local disk. The application is also able to encrypt an entire volume or partition, which is very useful if there are sensitive information on the USB drive, for example. The encrypted volume is seen by the system as a typical hard and has all the features, being necessary only to enter the password associated with the volume at the time of "montage".
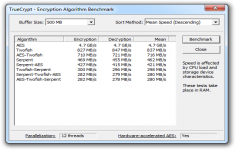
The software also includes hardware acceleration for encryption and decryption of AES algorithm. Enabled by default , this small revolution concerns only the recent Intel processors with the necessary capabilities : Intel Core i7- 980X , Intel Core i7 -970 , Intel Core i5- 650, Intel Core i5- 655K , Intel Core i5- 660, Intel Core i5 -661 , Intel Core i5 -670 , Intel Core i5 -680 and more, the speed of encoding and decoding being up to 8 times faster.
A volume can be mounted directly under Windows subject to provide the correct password. It is possible to create partitions and storage devices encrypted on the hard disk sectors with 4096, 2048 or 1024 bytes.
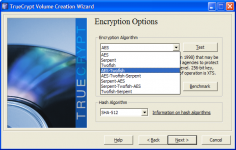
Many standard algorithms are supported by TrueCrypt, such as AES-256, Blowfish, CAST5, Serpent, Triple DES, and Twofish.
- Title:
- TrueCrypt 4.3a
- File Size:
- 1.5 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / XP64 / Vista64 / Windows7 64 / Windows8 / Windows8 64
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 07 May 2007
- Publisher:
- TrueCrypt Foundation
- Homepage:
- http://www.truecrypt.org
- MD5 Checksum:
- 58D4DB75C18B9FBED8B7857485176491
Improvements:
- Full support for custom screen DPI settings. (Windows, GUI)
- Other minor improvements. (Windows and Linux)
Bug fixes:
- Fixed bug that in some cases caused the 'Safely Remove Hardware' function to fail.
- In Windows Vista, it is now possible to read data from file-hosted TrueCrypt volumes located on UDF-formatted media mounted in read-only mode.
- All Volume Creation Wizard GUI elements are now correctly displayed on systems with custom DPI settings. (Windows, GUI)
- Other minor bug fixes. (Windows and Linux)
Security improvements:
- Linux: When running without administrator privileges, TrueCrypt automatically attempts to elevate its access rights (if necessary) using the sudo command. The Linux version of TrueCrypt no longer supports the set-euid root mode of execution. These changes also prevent all discovered and undiscovered (if any) security issues related to the set-euid root mode of execution, including an issue affecting all previous Linux versions of TrueCrypt where a local non-administrator user could cause a denial of service or gain administrator privileges.
Miscellaneous:
- If dismount is forced on a TrueCrypt volume when TrueCrypt runs in traveller mode, the TrueCrypt driver will not be unloaded when TrueCrypt exits (it will be unloaded only when the system is restarted or shut down). This prevents various problems caused by a bug in Windows (for instance, it would be impossible to start TrueCrypt again as long as there are applications using the dismounted volume). (Windows)
Related software
2.2/5 from 179 users