Nmap 7.60
Nmap 7.60
Gordon Lyon - ( Open Source)
Nmap is a powerful and indispensable tool for all network administrators developed to explore and perform an audit or a computer network hardware inventory.
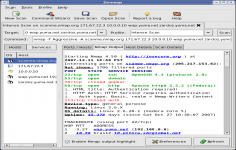
Nmap ("Network Mapper") is a software application that allows to detect open ports as well as information on a remote computer. Network administrators can use to identify the network status, manage schedules update services and monitor the availability of each item.
Using uses TCP, ICMP, IP or UDP it identifies services hosted on a computer. Thus, information such as the operating system or available ports can be accessed. Specific reports also allow to perform a specific audit of the safety and security of the system.
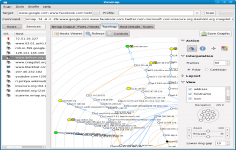
The functional graphical user interface provides access to a wealth of information at the first glance.
- Title:
- Nmap 7.60
- File Size:
- 26.1 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows 7 / XP 64-bit / Vista 64-bit / Windows 7 64-bit / Windows 8 / Windows 8 64-bit / Windows 10 / Windows 10 64-bit
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 02 Aug 2017
- Publisher:
- Gordon Lyon
- Homepage:
- http://nmap.org
- MD5 Checksum:
- B90A1A11071A63BAF5C3AB8606305DE8
[Windows] Updated the bundled Npcap from 0.91 to 0.93, fixing several issues with installation and compatibility with the Windows 10 Creators Update.
[NSE]NSE scripts now have complete SSH support via libssh2, including password brute-forcing and running remote commands.
[NSE] Added 14 NSE scripts from 6 authors, bringing the total up to 579! The summaries are below:
Ftp-syst sends SYST and STAT commands to FTP servers to get system version and connection information.
Http-vuln-cve2017-8917 checks for an SQL injection vulnerability affecting Joomla! 3.7.x before 3.7.1
Iec-identify probes for the IEC 60870-5-104 SCADA protocol.
Openwebnet-discovery retrieves device identifying information and number of connected devices running on openwebnet protocol.
Puppet-naivesigning checks for a misconfiguration in the Puppet CA where naive signing is enabled, allowing for any CSR to be automatically signed.
Smb-protocols discovers if a server supports dialects NT LM 0.12 (SMBv1), 2.02, 2.10, 3.00, 3.02 and 3.11. This replaces the old smbv2-enabled script.
Smb2-capabilities lists the supported capabilities of SMB2/SMB3 servers.
Smb2-time determines the current date and boot date of SMB2 servers.
Smb2-security-mode determines the message signing configuration of SMB2/SMB3 servers.
Smb2-vuln-uptime attempts to discover missing critical patches in Microsoft Windows
Systems based on the SMB2 server uptime.
Ssh-auth-methods lists the authentication methods offered by an SSH server.
Ssh-brute performs brute-forcing of SSH password credentials.
Ssh-publickey-acceptance checks public or private keys to see if they could be used to log in to a target. A list of known-compromised key pairs is included and checked by default.
Ssh-run uses user-provided credentials to run commands on targets via SSH.
[NSE] Removed smbv2-enabled, which was incompatible with the new SMBv2/3 improvements. It was fully replaced by the smb-protocols script.
[Ncat]Added Datagram TLS (DTLS) support to Ncat in connect (client) mode with --udp --ssl. Also added Application Layer Protocol Negotiation (ALPN) support with the --ssl-alpn option.
Updated the default ciphers list for Ncat and the secure ciphers list for Nsock to use "!aNULL:!eNULL" instead of "!ADH". With the addition of ECDH ciphersuites, anonymous ECDH suites were being allowed.
[NSE]Fix ndmp-version and ndmp-fs-info when scanning Veritas Backup Exec Agent 15 or 16.
[NSE]Added new SMB2/3 library and related scripts.
[NSE]Added wildcard detection to dns-brute. Only hostnames that resolve to unique addresses will be listed.
[NSE]FTP scripts like ftp-anon and ftp-brute now correctly handle TLS-protected FTP services and use STARTTLS when necessary.
[NSE]Function url.escape no longer encodes so-called "unreserved" characters, including hyphen, period, underscore, and tilde, as per RFC 3986.
[NSE]Function http.pipeline_go no longer assumes that persistent connections are supported on HTTP 1.0 target (unless the target explicitly declares otherwise), as per RFC 7230.
[NSE]The HTTP response object has a new member, version, which contains the HTTP protocol version string returned by the server, e.g. "1.0".
[NSE]Fix handling of the objectSID Active Directory attribute by ldap.lua.
[NSE] Fix line endings in the list of Oracle SIDs used by oracle-sid-brute. Carriage Return characters were being sent in the connection packets, likely resulting in failure of the script.
[NSE]http-useragent-checker now checks for changes in HTTP status (usually 403 Forbidden) in addition to redirects to indicate forbidden User Agents.