Nmap 6.40
Nmap 6.40
Gordon Lyon - (Open Source)
Nmap is a powerful and indispensable tool for all network administrators developed to explore and perform an audit or a computer network hardware inventory.
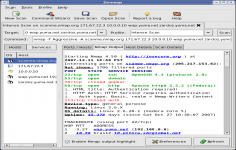
Nmap ("Network Mapper") is a software application that allows to detect open ports as well as information on a remote computer. Network administrators can use to identify the network status, manage schedules update services and monitor the availability of each item.
Using uses TCP, ICMP, IP or UDP it identifies services hosted on a computer. Thus, information such as the operating system or available ports can be accessed. Specific reports also allow to perform a specific audit of the safety and security of the system.
The functional graphical user interface provides access to a wealth of information at the first glance.
- Title:
- Nmap 6.40
- File Size:
- 25.5 MB
- Requirements:
- Windows 2000 / XP / Vista / Windows7 / XP64 / Vista64 / Windows7 64 / Windows8 / Windows8 64
- Language:
- en-us
- License:
- Open Source
- Date Added:
- 29 Jul 2013
- Publisher:
- Gordon Lyon
- Homepage:
- http://nmap.org
- MD5 Checksum:
- 2AF7D54A09E9C36D704CB3A2DE28AFF3
- [Nping] Nping now checks for a matching ICMP ID on echo replies, to avoid receiving crosstalk from other ping programs running at the same time.
- [NSE] Added http-adobe-coldfusion-apsa1301.nse. It exploits an authentication bypass vulnerability in Adobe Coldfusion servers.
- [NSE] The ipOps.isPrivate library now considers the deprecated site-local prefix fec0::/10 to be private.
- [Ncat] Added --lua-exec. This feature is basically an equivalent of ncat --sh-exec "lua " and allows you to run Lua scripts with Ncat, redirecting all stdin and stdout operations to the socket connection.
- [NSE] Oops, there was a vulnerability in one of our 437 NSE scripts. If you ran the (fortunately non-default) http-domino-enum-passwords script with the (fortunately also non-default) domino-enum-passwords.idpath parameter against a malicious server, it could cause an arbitrarily named file to to be written to the client system. stdnse.filename_escape function for extra safety.
- [NSE] Added teamspeak2-version.nse
- Nmap's routing table is now sorted first by netmask, then by metric. Previously it was the other way around, which could cause a very general route with a low metric to be preferred over a specific route with a higher metric.
- [Ncat] The -i option (idle timeout) now works in listen mode as well as connect mode.
- Fixed a byte-ordering problem on little-endian architectures when doing idle scan with a zombie that uses broken ID incremements.
- [Ncat] Ncat now support chained certificates with the --ssl-cert option.
- Stop parsing TCP options after reaching EOL in libnetutil.
- [NSE] The dns-ip6-arpa-scan script now optionally accepts "/" syntax for a network mask.
- [Ncat] Reduced the default --max-conns limit from 100 to 60 on Windows, to stay within platform limitations.
- Fixed IPv6 routing table alignment on NetBSD.
- [NSE] Added http-phpmyadmin-dir-traversal
- Added a service probe for Erlang distribution nodes.
- Updated libdnet to not SIOCIFNETMASK before SIOCIFADDR on OpenBSD. This was reported to break on -current as of May 2013.
- Fixed address matching for SCTP (-PY) ping.
- Removed some non-ANSI-C strftime format strings ("%F") and locale-dependent formats ("%c") from NSE scripts and libraries. C99-specified %F
- [Zenmap] Added Polish translation
- [NSE] Added http-coldfusion-subzero. It detects Coldfusion 9 and 10 vulnerable to a local file inclusion vulnerability and grabs the version, install path and the administrator credentials.
- [Nsock] Added a minimal regression test suite for nsock.
- [NSE] Updated redis-brute.nse and redis-info.nse to work against the latest versions of redis server.
- [Ncat] Fixed errors in conneting to IPv6 proxies.
- Added a service probe for Minecraft servers.
- [NSE] Updated hostmap-bfk to work with the latest version of their website.
- [NSE] Added XML structured output support to hostmap-bfk, hostmap-robtex, and hostmap-ip2hosts.
- [NSE] Added hostmap-ip2hosts. It uses the service provider ip2hosts.com to list domain names pointing to the same IP address.
- [NSE] Added http-vuln-cve2013-0156. It detects Ruby on Rails servers vulnerable to remote command execution.
- Added a service probe for the Hazelcast data grid.
- [NSE] Rewrote telnet-brute for better compatibility with a variety of telnet servers.
- [Nsock] Added initial proxy support to nsock. Nsock based modules (version scan, nse) of nmap can now establish TCP connections through chains of proxies. HTTP CONNECT and SOCKS4 protocols are supported, with some limitations.
- Fixed a regression that changed the number of delimiters in machine output.
- [Zenmap] Updated the Italian translation.
- Handle ICMP type 11 (Time Exceeded) responses to port scan probes. Ports will be reported as "filtered", to be consistent with existing Connect scan results, and will have a reason of time-exceeded.
- Add new decoders (BROWSER, DHCP6 and LLMNR) to broadcast-listener and changed output of some of the decoders slightly.
- Timeout script-args are now standardized to use the timespec that Nmap's command-line arguments take (5s, 5000ms, 1h, etc.). Some scripts that previously took an integer number of milliseconds will now treat that as a number of seconds if not explicitly denoted as ms.
- The list of nameservers on Windows now ignores nameservers from inactive interfaces.
- Namespace the pipes used to communicate with subprocesses by PID, to avoid multiple instances of Ncat from interfering with each other.
- Nmap may now partially rearrange its target list for more efficient host groups. Previously, a single target with a different interface, or with an IP address the same as a that of a target already in the group, would cause the group to be broken off at whatever size it was. Now, we buffer a small number of such targets, and keep looking through the input for more targets to fill out the current group.
- [NSE] Changed ip-geolocation-geoplugin to use the web service's new output format.
- Limited the number of open sockets in ultra_scan to FD_SETSIZE. Very fast connect scans could write past the end of an fd_set and cause a variety of crashes: nmap: scan_engine.cc:978: bool ConnectScanInfo::clearSD(int): Assertion `numSDs > 0' failed. select failed in do_one_select_round(): Bad file descriptor (9)
- Fixed a bug that prevented Nmap from finding any interfaces when one of them had the type ARP_HDR_APPLETALK; this was the case for AppleTalk interfaces. However, This support is not complete since AppleTalk interfaces use different size hardware addresses than Ethernet. Nmap IP level scans should work without any problem
- [Nping] Nping now skips localhost targets for privileged pings (with an error message) because those generally don't work.
- [Ncat] Ncat now keeps running in connect mode after receiving EOF from the remote socket, unless --recv-only is in effect.
- Routes are now sorted to prefer those with a lower metric. Retrieval of metrics is supported only on Linux and Windows. [David Fifield]
- Packet trace of ICMP packets now include the ICMP ID and sequence number by default.
- [NSE] Added ike-version and a new ike library
- [NSE] Fixed various NSEDoc bugs
- [Zenmap] Zenmap now understands the NMAP_PRIVILEGED and NMAP_UNPRIVILEGED environment variables.
- It's now possible to mix IPv4 range notation with CIDR netmasks in target specifications. For example, 192.168-170.4-100,200.5/16 is effectively the same as 192.168.168-170.0-255.0-255.
- Added nmap-fo.xsl, This converts Nmap XML into XSL-FO, which can be converted into PDF using Apache FOP.
- Increased the number of slack file descriptors not used during connect scan. Previously, the calculation did not consider the descriptors used by various open log files. Connect scans using a lot of sockets could fail with the message "Socket creation in sendConnectScanProbe: Too many open files".
- [Zenmap] Fixed internationalization files. Running in a language other than the default English would result in the error "ValueError: too many values to unpack".
- Changed the --webxml XSL stylesheet to point to the new location of nmap.xsl in the new respository,
- [NSE] Made the vulnerability library able to preserve vulnerability information across multiple ports of the same host.
- [NSE] Added ventrilo-info, This gets information from a Ventrilo VoIP server.
- Removed the undocumented -q option, which renamed the nmap process to something like "pine".
- Moved the Japanese man page from man1/jp to man1/ja. jp is a country code while ja is a language code.
- [NSE] Added mysql-enum script which enumerates valid mysql server usernames
- [Nsock] Reworked the logging infrastructure to make it more flexible and consistent. Updated nmap, nping and ncat accordingly. Nsock log level can now be adjusted at runtime by pressing d/D in nmap.
- [NSE] Fixed scripts using unconnected UDP sockets.
- [NSE] Added structured output to http-git.nse.
- [NSE] Added murmur-version, This gets the server version and other information for Murmur, the server for the Mumble VoIP system.
- Added a corresponding UDP payload for Murmur.
- [Zenmap] Fixed a crash that could be caused by opening the About dialog, using the window manager to close it, and opening it again.
- [Ncat] Made test-addrset.sh exit with nonzero status if any tests fail. This in turn causes "make check" to fail if any tests fail.
- Fixed compilation with --without-liblua.
- Fixed CRC32c calculation (as used in SCTP scans) on 64-bit platforms.
- [NSE] Added multicast group name output to broadcast-igmp-discovery.nse.
- [NSE] Added new fingerprints for http-enum: Sitecore, Moodle, typo3, SquirrelMail, RoundCube.